VPN Mastery Guide: Optimizing Company Network Access with AWS Client VPN
VPN Mastery Guide: Optimizing Company Network Access with AWS Client VPN
Introduction
AWS Client VPN is a managed client-based VPN service that enables you to securely access your AWS resources and resources in your on-premises network. With Client VPN, you can access your resources from any location using an OpenVPN-based VPN client.
Today, we will be discussing how to set up AWS Client VPN by Terraform and describe the process of connecting to the VPN from a client machine.
This is the first part of the series of articles about AWS Client VPN. \
Prerequisites
- AWS Account
- Terraform (latest version)
- OpenVPN client (https://openvpn.net/client/)
- AWS CLI (latest version)
- AWS CLI profile configured with access to your AWS account
- Existed VPC with public subnets and private subnets.
Details of AWS Client VPN
Features
AWS Client VPN supports the following features:
- Mutual authentication: AWS Client VPN supports mutual authentication with certificate-based clients for a more secure VPN connection.
- Active Directory: AWS Client VPN supports Active Directory authentication for Windows-based clients.
- Federated authentication: AWS Client VPN supports federated authentication with the Security Assertion Markup Language (SAML) 2.0 standard.
We will be using mutual authentication in this article.
Mutual authentication
Mutual authentication performs like belows:
- Mutual authentication requires that the client and the server have a certificate that is signed by a common certificate authority (CA).
- The client presents its certificate to the server during authentication.
- The server validates the client certificate and authenticates the client.
You can use AWS managed certificate authority (ACM) to generate the certificate, but it is not free. We can use easy-rsa to generate the client certificate and server certificate as AWS suggests.
Use easy-rsa to generate the client certificate and server certificate
Easy-RSA is a utility for managing X.509 PKI, an X.509 certificate binds an identity to a public key using a digital signature.
Pricing
AWS Client VPN endpoint association $0.10 per hour
AWS Client VPN connection $0.05 per hour
Architecture
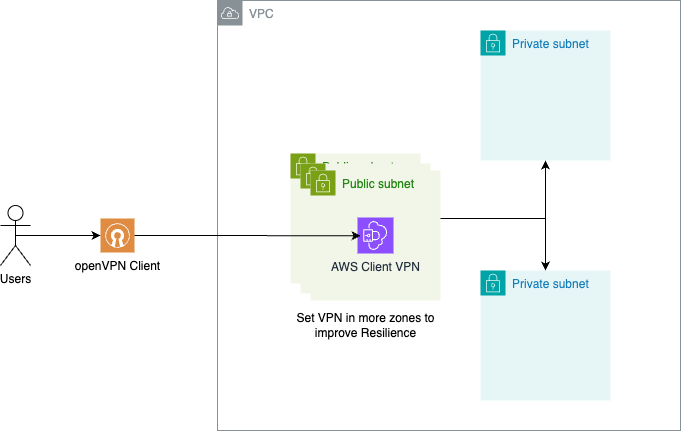
Architecture diagram of AWS Client VPN, set VPN in multiple zones to improve resilience
Steps
Create a server cert and client certs
- Install easy-rsa.
- Generate the CA certificate and key.
1
2
3
4after theres commands you will get the ca.crt and ca.key in the pki/ca directory
cd easy-rsa/easyrsa3
./easyrsa init-pki
./easyrsa build-ca - Generate the server certificate and key.
1
2
3
4
5after theres commands you will get the server.crt and server.key in the pki/issued directory
we will upload the server.crt to AWS certificate manager to create a server certificate
and then use it to create the AWS Client VPN.
cd easy-rsa/easyrsa3
./easyrsa build-server-full server - Generate the client certificate and key.
1
2
3
4after theres commands you will get the client.crt and client.key in the pki/issued directory
you should create a client name for each client (colleagues in your company!)
cd easy-rsa/easyrsa3
./easyrsa build-client-full <client-name>
Upload the server certificate to AWS Certificate Manager
1 | aws acm import-certificate --certificate fileb://server.crt --private-key fileb://server.key --certificate-chain fileb://ca.crt``` |
Create a Client VPN endpoint
1 | resource "aws_security_group" "test" { |
How to use AWS Client VPN.
Send the client certificate and key to your colleagues, and they can use the OpenVPN client to connect to the VPN.
Read this page to know how to export the client certificate and key.
